PriNIST, AI & ML supported
On Screen Data Protection software
Protects sensitive information being leaked over
screen sharing with patent pending SaaS and
On-premise solutions.
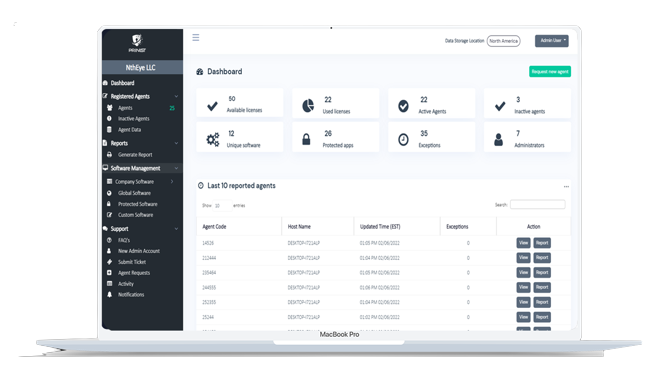
PriNIST Features
PriNIST covers the most important features required by legal and technology departments.
Artificial Intelligence
PriNIST applies Machine Learning (ML) and Artificial Intelligence (AI) to identify sensitive data storing applications and provide recommendations.
On Demand Protection
Easy to use interface and advanced technologies apply protection on an enterprise as soon as it is created in the PriNIST portal with zero hinderance to the end point user.
Audit Reports
PriNIST complies with many global data security and privacy regulations [GDPR, NIST, HIPAA, CCPA, PCI DSS, SOX, LGPD, GLBA, POPI] and provides detailed reports to be acted upon.
Data Region Segregation
PriNIST SaaS architecture is designed to support data segregation requirements to comply various global data security and privacy requirements.
Exception Management
PriNIST is a compliance friendly solution and is tailored to provide exclusive control on end points while ensuring industry accepted exception management.
On Premise Software Support
PriNIST provides technical expertise in enterprise environments to deploy, test and manage an on-premise implementation.
PriNIST Use Cases
Learn about use cases against threats involved in intentional, unintentional, infected or malicious screen sharing.
Employee Fraud Prevention
In the recent years, unskilled employees/contractors have been using external job support agencies or individuals to act on their behalf which/who can connect to the enterprise end point using a screen sharing software and take control over the mouse and keyboard. By doing so, an employee/contractor unknowingly violates the organization’s polices while exposing an enterprise’s confidential information.
Certain Zero Day Malware Protection
Enterprises, government organizations, NGOs, non-profit organizations are the targets of malicious attackers (can be a state sponsored actor or an extremely motivated hacker). Certain zero-day malwares are designed to bypass existing defense mechanisms and transmit user related data to attackers. Especially, by taking screenshots or recording target screen and sending the payload via stealth or exploited channels.
Accidental Data Exposure
Today’s enterprises must use virtual meetings to communicate with their employees and share their screens to present certain data or applications to the participants. However, when a user tries to share their desktop or applications, most of the time they share certain information which they are not supposed to share. By doing so meeting organizer unknowingly exposes or shares restricted/confidential information to unintended users which results in a great amount of data leakage/loss.
Outsourcing Data Leakage
Technology process out sourcing is the most common business requirement for many organizations and they try to protect their interest with various agreements and available technology controls. One of the critical functions is end user support, which allows support personnel to connect to user desktops to provide various support such as passwords, application installs etc. On the negative side, when a support personnel connects to the end user’s computer/desktop he can see certain documents that may contain sensitive information.
Espionage scenarios
Nations and their technology infrastructure are under attack by state sponsored actors, international competitors, hackers etc. When international state sponsored actors are injected into the company to act as employees/contractors, who can leak confidential information via stealthy channels like web based (WebRTC) screensharing applications, unfortunately, their acts are not being prevented by current Data Loss Prevention / End Point Protection tools resulting in loss of most protected or sensitive data.
Intellectual property leakage
The existing DLP tools and technologies do not solve the problems that PriNIST is solving today. Especially, when it comes to confidential data that is being operated in end user computing environment from intentional and unintentional data leaks in screen or data streaming situations.
News
Russian Hackers Broke Into Federal Agencies, U.S. Officials Suspect
In one of the most sophisticated and perhaps largest hacks in more than five years, email systems were breached at the Treasury and Commerce Departments.
Read moreIndia, China in US’ black list for IP theft
The “black list” includes 11 countries, Algeria, Argentina, Chile, China, India, Indonesia, Kuwait, Russia, Saudi Arabia, Ukraine and Venezuela, the Efe news reported
Read moreIQE files against Tower Semiconductor claiming theft of trade secrets
Wafer company says it has 'significant reason' to believe Israeli chipmaker misappropriated IP
Read moreFrequently Asked Questions
Still having questions? Contact us with just a click.
PriNIST is the only advanced fraud management and on-screen data leak prevention solution. It is designed to protect an organization’s intellectual property from ever evolving threats. It is a SaaS and On-premise solution for data leakage/loss and malicious malware threats. It is designed to prevent advanced threat vectors like intentional and unintentional data leakages.
-
Accidental data exposure
-
Associate fraud prevention
-
Outsourcing data leakage scenarios
-
Certain zero-day malware protection
-
Espionage scenarios
-
Intellectual property leakage
- SOX (Sarbanes-Oxley Act)
- NIST (National Institute of Standards and Technology) guidelines
- GDPR (General Data Protection Regulation)
- LGPD (Lei Geral de Proteção de Dados Pessoais)
- POPI (Protection of Personal Information)
- CCPA (California Consumer Privacy Act)
- GLBA (Gramm–Leach–Bliley Act)
- HIPAA (Health Insurance Portability and Accountability Act)
- ADPR (Australia)
- HITRUST (Health Information Trust Alliance)
- ISO 27001 and 27701 (International Organization for Standardization)
- PCI DSS (Payment Card Industry Data Security Standard)
- PDPA (Personal Data Protection Act)
- PIPEDA (Personal Information Protection and Electronic Documents Act
Yes, PriNIST is a cloud-based solution. PriNIST has two variants- a cloud-based and an On-premise solution.
Yes, PriNIST supports advanced exception management.
Yes, PriNIST has managed services offerings. The managed services are as follows:
-
Installation and uninstallation support
-
Troubleshooting
-
Routine maintenance
-
Role based support
-
End-user support
-
Proactive compliance monitoring
-
PriNIST server management
-
PriNIST infrastructure design
-
PriNIST managed hosting services
-
PriNIST managed security
-
Strategic security IT consultancy
-
Data protection security assessments
-
Block chain security services
-
API penetration testing
-
Secure code review
PriNIST supports all the Microsoft Windows OS [Mac and Linux release scheduled for third quarter of 2023]








